systemd journals play a crucial role in the Linux system ecosystem, and understanding the importance of the logs contained within is essential for both system administrators and developers.
For those unfamiliar, systemd is an init system employed by Linux distributions, initiates the user space and oversees all ensuing processes. One of its key components, systemd journal, assumes a central role in logging system activities and messages, delivering a host of benefits to both system administrators, developers and cyber security engineers. The systemd journal functions as a logging system that gathers, archives, and oversees log messages and event data originating from a diverse array of system components, encompassing the kernel, system services, applications, and user activities.
Why is it a must use tool for your infrastructure monitoring?
Given the rich and structured information systemd journals provide, they are an essential tool for anyone responsible for maintaining, monitoring, or developing applications and services for Linux systems. Properly managed and analyzed, they can offer deep insights into system health, performance, and security.
Here are the primary reasons why these logs are so important, from a security perspective:
-
Audit Trail
systemdjournals provide an audit trail, recording user actions, system and applications events, and related activities. This is invaluable for tracking unauthorized or unexpected changes and actions. -
Intrusion Detection
Any unauthorized or malicious activity, like multiple failed login attempts or unexpected service activations, can be identified by monitoringsystemdlogs. -
Forensics
In the event of a system breach or failure,systemdlogs are the most crucial part of the forensic process, helping to recreate the sequence of events leading up to the incident. -
Immutable Logs
systemdjournals ensure that once a log entry is made, it’s unchangeable. This safeguards the authenticity of historical records. Even in the event of a system breach, attackers cannot modify existing logs, ensuring a reliable record for security assessments. -
Structured Logs
Unlike traditional log files which are unstructured,systemdjournals store entries in a structured binary format. This ensures logs are uniformly organized with explicit fields, simplifying parsing and analysis, and ensuring data consistency across entries. -
Compliance
For organizations that need to adhere to certain regulatory standards (e.g., HIPAA, SOX, GDPR),systemdlogs provide evidence of compliance by maintaining a record of system and user activity. -
Accountability
systemdjournal logs can be used to ensure that operational standards are being followed, especially in environments with multiple administrators or users.
On the operational side, when something goes wrong—be it a service crash or system malfunction—the first place most administrators look is the logs. systemd journals provide detailed logs that can help diagnose the root cause of issues, identify usage patterns in recurring issues, and highlight service dependencies.
Continuous monitoring of systemd journals can help administrators spot potential issues before they become critical. This includes identifying deprecated configurations, services nearing resource limits, or suspicious activities.
Application developers can also benefit from systemd journal logs when debugging application issues in a live environment. These logs can provide context about the system state and other running services that might influence application behavior.
Centralized Logs Management
In a multi-server or distributed system environment, the complexity of log management increases exponentially. Each server or service may generate its own set of logs, and keeping track of all these disparate logs can be challenging. This is where centralized logging becomes pivotal.
By consolidating logs from various servers into one place, administrators gain a holistic view of the entire infrastructure. This facilitates efficient cross-referencing of events, eases the determination of root causes, and streamlines monitoring and alerting.
Centralizing systemd journal logs ensures a unified, secure, and integrated approach to log management:
-
Unified Infrastructure wide view
Gathering logs from multiple sources and systems into a single, unified dashboard, makes monitoring and analysis significantly easier. -
Real-time Threat Detection
Monitoring logs for suspicious activities, multiple failed login attempts, unusual data transfers, etc., providing the ability to detect potential security threats in real-time. -
Data Integrity
Moving logs to a central place in real-time, can ensure that logs are available and not tampered.systemdjournals offer cryptographic signing or hashing of logs to guarantee their integrity. -
Compliance Adherence
Many regulations require organizations to maintain logs for specific durations and ensure that they are tamper-proof.systemdjournal can help meet these requirements. -
Retention & Archival
A centralized logs management system provides control over how long logs are retained and ensures older logs are archived for future reference or compliance needs.
A logs management system isn’t just a repository for raw data; it’s a powerful tool that can offer invaluable insights into operations and security.
systemd journal is the right tool for security
systemd journals are designed to be an integrated and robust logging solution for modern Linux systems and they offer some important security features that aim to ensure the confidentiality, integrity, and authenticity of logs:
Log Sealing
When systemd journals are configured to use log sealing, cryptographic techniques are employed to sign the journal files. Here’s why that’s important:
-
Integrity
By sealing the journal files, any tampering or modification of the log data can be detected. If someone tries to alter a log entry, the signature verification will fail. -
Authenticity
It ensures that the logs were genuinely written by the system and not injected or fabricated by an attacker. The signature can serve as a proof of the origin of the logs.
Forward-Secure Sealing (FSS)
Forward-secure sealing takes log sealing a step further. The idea behind FSS is that even if an attacker manages to compromise the current cryptographic key, they should not be able to retroactively tamper with past logs without detection.
-
How it works
Forward-secure sealing uses a cryptographic technique that involves evolving the cryptographic keys over time. After a set interval,journaldwill “forget” the old key and generate a new one. Even if the latest key is compromised, it can’t be used to alter or fake signatures from earlier intervals because those old keys are no longer available. -
Security against key compromise
This ensures that even if a system’s security is breached and the current key is exposed, attackers cannot use that key to alter past logs in a way that makes them appear legitimate. Only logs signed after the breach could be tampered with, but logs prior to that remain secure.
To learn how to enable FSS, click here.
Of course, cryptographically sealing logs can add some overhead. Depending on the scale and volume of logs, and the system’s performance, this overhead might be negligible or significant.
Furthermore, journald rate-limits the messages it receives. This can prevent log flooding, which can be used as a form of DoS attack or to bury meaningful log entries in noise.
systemd journals use LZ4 compression for all journal files. This not only saves disk space but also provides a form of lightweight obfuscation. Though compression is not encryption, it does make plain text log scraping harder for someone who might gain unauthorized access to the journal files.
Unlike traditional log files which are predominantly text, journald logs are stored in a binary, structured format. This means that logs contain explicit fields (like _UID, _PID, etc.), making them not only more consistent but also more resistant to log injection attacks where malicious actors might try to insert fake log entries.
And as expected from a modern logs management systemd, systemd journald handles automatic rotation of journal files and can enforce policies regarding how much log data is retained. This can be specified in terms of storage space used or time. Automatically discarding old logs can help ensure that sensitive data does not linger on systems indefinitely.
And in cases, this is required, users can specify where journal logs should be stored: in volatile memory (e.g., /run/log/journal/), on disk (/var/log/journal/), or both. Storing logs in volatile memory means they are automatically wiped on system reboot, which can be a feature for systems where persisting logs might be a security concern.
In summary, systemd journal incorporates multiple features designed to enhance the security posture of log data. When used correctly, and in combination with other system security practices, it provides a reliable and secure logging solution.
systemd journals with Netdata
Using systemd journals together with Netdata offers significant advantages:
-
Native Integration
Being native to most Linux systems,systemdjournal captures logs directly and from the earliest boot stages, which external systems might miss.While not a feature of
journaldper se, its tight integration with the system means it can log actions and decisions made by Linux Security Modules like SELinux or AppArmor, providing an audit trail for system security decisions. -
Consistent Format
Logs stored in thesystemdjournals have a consistent format, which can simplify parsing and analysis. -
Metadata Tagging
systemdjournals come with rich metadata, which can be invaluable for filtering, searching, and categorizing logs. -
Flexibility
The dynamic and variable fields support allows each application to have its own unique fields, providing deep granularity. -
Performance
The binary format ofsystemdjournals can offer better performance and storage efficiency compared to text-based logs. -
Security
systemdjournals have built-in features like log sealing and forward-secure sealing, which enhance the security and integrity of the logs. -
Ease of Use
Netdata’s capabilities, such as PLAY mode, filtering, full-text search and zero configuration and maintenance (see a demo here), offer an intuitive and responsive user experience. -
Low Configuration Overhead
Netdata works directly on journal files without needing third-party components, and there’s no need to predefine which fields to index. -
Unified View on Centralization Server
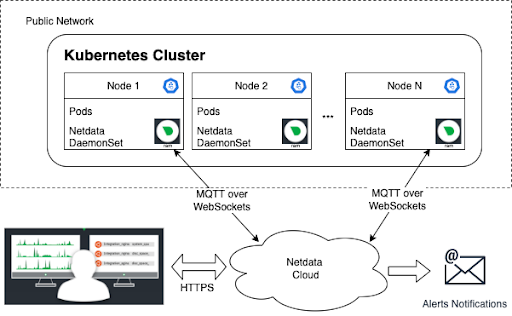
Netdata provides a unified view of all logs across the entire infrastructure, which can be crucial for quick diagnostics.
How systemd journal with Netdata compares to others
In the realm of logging and monitoring, each solution has its strengths. However, many popular systems present challenges and weaknesses that systemd journal with Netdata effortlessly overcomes. Here are a few:
-
Early Boot Logs
One of the common issues with logging systems not natively integrated into the Linux environment, such as Loki or traditional log files, is their potential to miss crucial early boot logs. Being inherent to the Linux system,systemdjournal doesn’t have this blind spot, ensuring comprehensive coverage from the start. -
Operational Costs and Complexity
ELK Stack, Splunk, and others often come with intricate configurations, and their enterprise versions have substantial licensing fees. Additionally, these systems might require extensive resources, which drives up infrastructure costs. In contrast, the open-source nature ofsystemdjournal and Netdata translates to minimal costs, both financially and operationally. -
Structured Logging
While Elasticsearch and similar tools offer a wide range of features, extracting precise insights can be cumbersome due to their reliance on diverse log formats and structures.systemdjournal‘s inherent structured logging means data is consistently organized, making parsing and analysis seamless. -
Performance Impact
Solutions like Splunk are known for their hefty resource demands, leading to potential performance degradation. Netdata, combined with the binary log format ofsystemdjournal, ensures minimal resource usage, preserving system performance. -
Robust Security Measures
Not all logging tools prioritize advanced security features. Loki, for example, focuses on lightweight logging but doesn’t offer the advanced security benefits ofsystemdjournal, such as log sealing and forward-secure sealing, crucial for ensuring log data remains tamper-proof. -
User Experience and Flexibility
Enterprise systems, like Splunk, offer a myriad of features but can overwhelm users with their complexity. The intuitive interface of Netdata, coupled with the rich metadata fromsystemdjournal, ensures users get in-depth insights without steep learning curves. -
True Centralized Logging
While many solutions promote centralized logging, ensuring consistency, security, and real-time access across a multi-server setup can be cumbersome. The seamless integration of Netdata withsystemdjournal offers a genuinely centralized experience, simplifying setup and monitoring.
While other solutions have their merits, systemd journal with Netdata addresses several common pain points, offering a reliable, efficient, and secure logging experience that many alternatives struggle to provide.